Table of contents
An enhanced version of honeypot-wasp with a fake username and password prompt.
Many websites provide administrative access to a management interface for the webmaster, mostly via a sub-directory called /admin and also /login.
In case your website does not have such a directory (or with a different name), you can create a fake one and use this honeypot to see the access attempts.
Installing the honeypot is simple.
-
Edit
honeypot-hornet.phpand change the name of the log file to something less guessable thanlogfile.txt.$file = 'logfile.txt';
-
Create an empty text file with that name.
-
Rename
honeypot-hornet.phptoindex.phporindex.html. -
Create the desired directory where you want to install the honeypot on your web server, e.g.
/admin. -
Upload the renamed file as well as the empty text file into that directory.
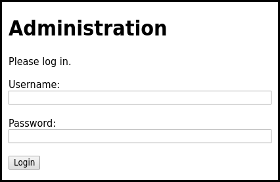 Use your web browser and navigate to the directory on your website which contains the honeypot file. It will show a login prompt asking for the username and password.
Use your web browser and navigate to the directory on your website which contains the honeypot file. It will show a login prompt asking for the username and password.
The login data can also be given via URL, for example:
https://www.foo.bar/admin?username=admin&password=asdf1234
- If a username other than
adminis given it will return that the user does not exist. - If you try logging in as
adminit will always return that the password foradminis invalid. - If no username and password is given it will simply ask to log in.
The allegedly failed attempts return the code 401 (Unauthorized).
After that the attempted login has been logged into the given log file. For example:
[2018-04-28 - 09:42:10] Attempt to log in at 'https://www.foo.bar/admin'
[2018-04-28 - 09:42:10] Login method: 'POST'
[2018-04-28 - 09:42:10] Username: 'admin'
[2018-04-28 - 09:42:10] Password: 'asdf1234'
[2018-04-28 - 09:42:10] IP address: 192.168.1.2
[2018-04-28 - 09:42:10] User agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.108 Safari/537.36
Any suggestions, questions, bugs to report or feedback to give?
You can contact me by sending an email to [email protected] or by opening a GitHub issue (which I would prefer if you have a GitHub account).