freeuse
Some useful codes and scripts
find_file.ps1 tested on powershell v5+
find_file.ps1 tested on powershell v5+This PowerShell script is designed to search for files across specified drives, filtering them based on their file extensions, and then returning information about the files.
Customization Options:
To show only counts: Set $showPaths = $false.
To process all files: Set $processAll = $true, and use $excludeExtensions to specify which file types to ignore.
To include specific file types: Use $includeExtensions to list the extensions you want to process, and set $processAll = $false.
To process all drives: Set $selectedDrives = @() to include all filesystem drives.
This script is flexible and allows detailed control over what types of files to search for, which drives to search, and whether to display full file paths or just counts.
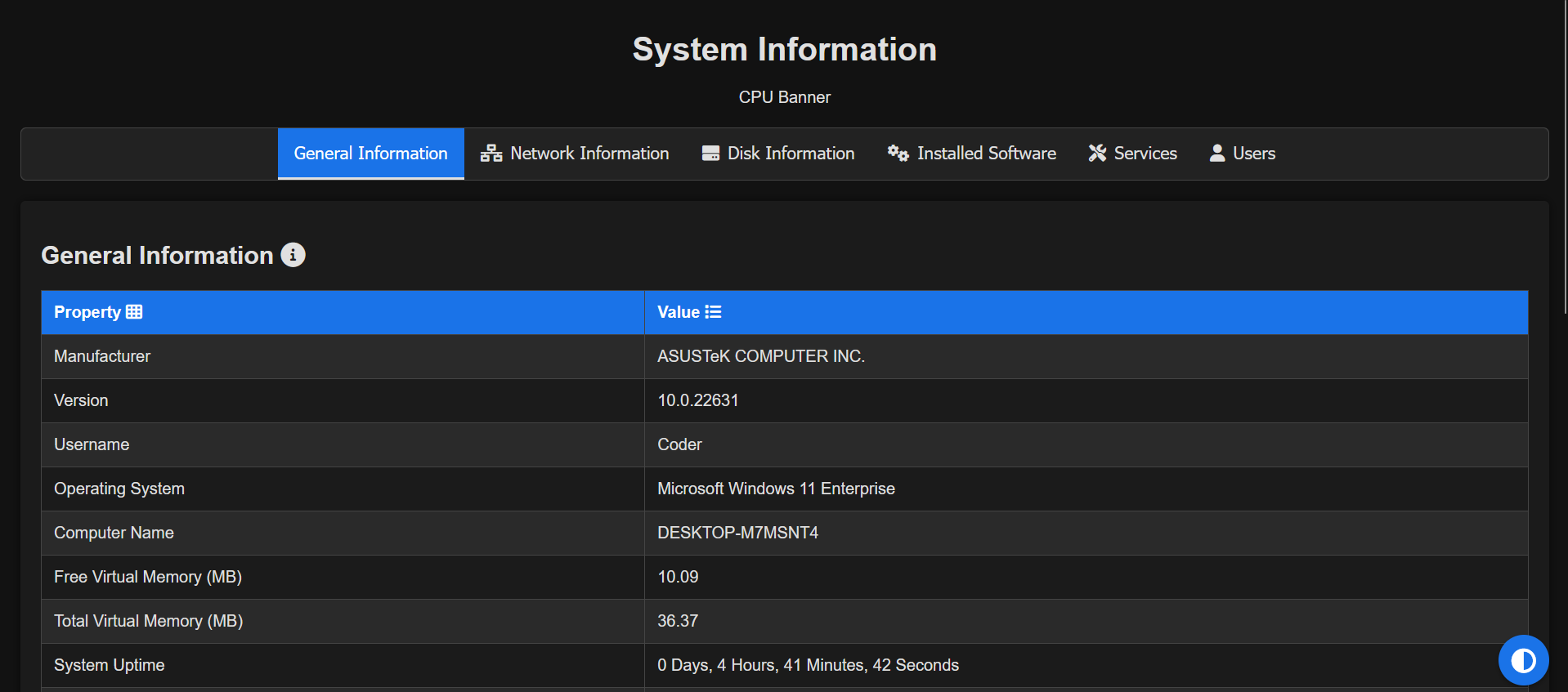
system_info.ps1 tested on powershell v5+
system_info.ps1 tested on powershell v5+This PowerShell script collects a variety of system information, formats it into an HTML page, and opens that page in the default web browser.
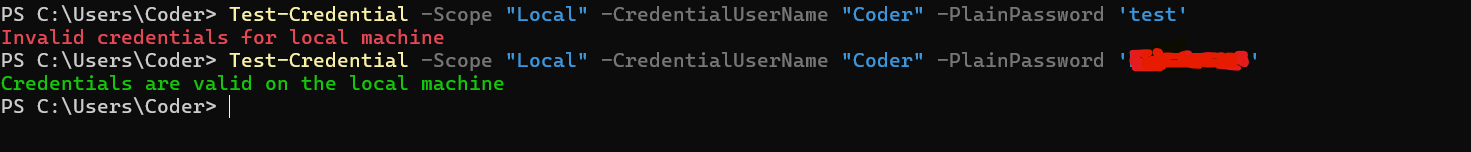
check_cred.ps1 tested on powershell v5+
check_cred.ps1 tested on powershell v5+Function to test credentials locally or remotely
Usage:
# Example usage for local testing with a plain-text password
Test-Credential -Scope "Local" -CredentialUserName "mohammad" -PlainPassword "MySecurePassword123"
# Example usage for remote testing with a plain-text password
Test-Credential -Scope "Remote" -ComputerName "RemoteServer01" -CredentialUserName "DOMAIN\Username" -PlainPassword "MySecurePassword123"
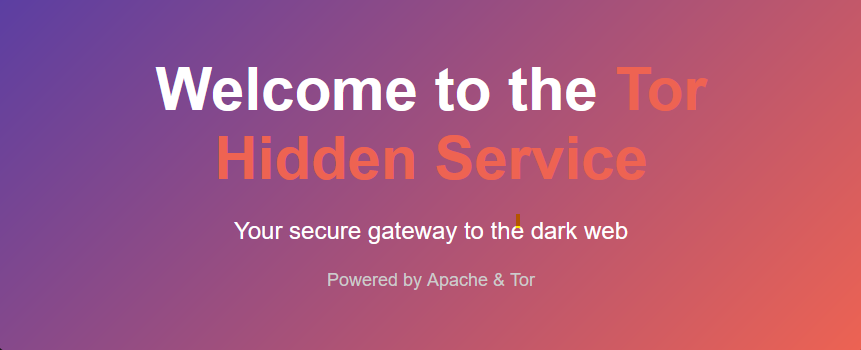
setup_tor_apache.sh tested on ubuntu 23
setup_tor_apache.sh tested on ubuntu 23The provided script automates the process of setting up a Tor hidden service using Apache on an Ubuntu system.
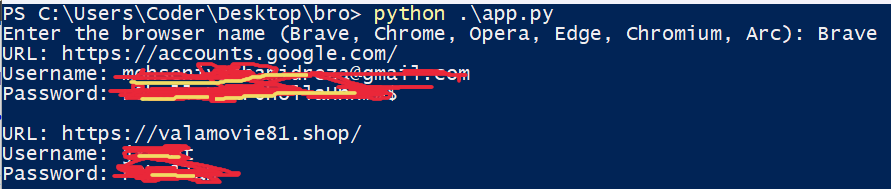
Browser_Password .py tested on Windows 11 Build 26100
Browser_Password .py tested on Windows 11 Build 26100This Python script is designed to extract and decrypt saved login credentials (i.e., usernames and passwords) from several popular Chromium-based browsers, including Brave, Chrome, Opera, Edge, Chromium, and Arc. The script targets the Login Data database file and uses the Local State file for decryption keys, leveraging the AES encryption used by these browsers.