-
Notifications
You must be signed in to change notification settings - Fork 274
Installation
Jakub Jareš wrote an excellent introduction to module installation, so I decided to adapt his example for PowerForensics.
To begin open an internet browser and navigate to the main PowerForensics github page. Once on this page you will need to download and extract the module into your modules directory.
If you used Internet Explorer to download the archive, you need to unblock the archive before extraction, otherwise PowerShell will complain when you import the module. If you are using PowerShell 3.0 or newer you can use the Unblock-File cmdlet to do that:
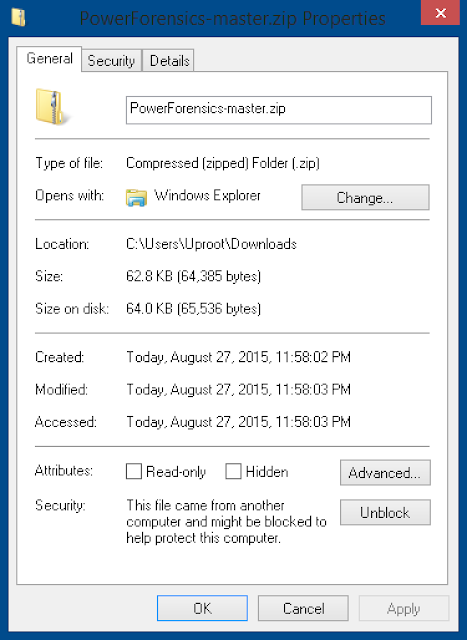
Unblock-File -Path "$env:UserProfile\Downloads\PowerForensics-master.zip"If you are using an older version of PowerShell you will have to unblock the file manually. Go to your Downloads folder and right-click PowerForensics-master.zip and select "Properties". On the general tab click Unblock and then click OK to close the dialog.
Open your Modules directory and create a new folder called PowerForensics. You can use this script to open the correct folder effortlessly:
function Get-UserModulePath {
$Path = $env:PSModulePath -split ";" -match $env:USERNAME
if (-not (Test-Path -Path $Path))
{
New-Item -Path $Path -ItemType Container | Out-Null
}
$Path
}
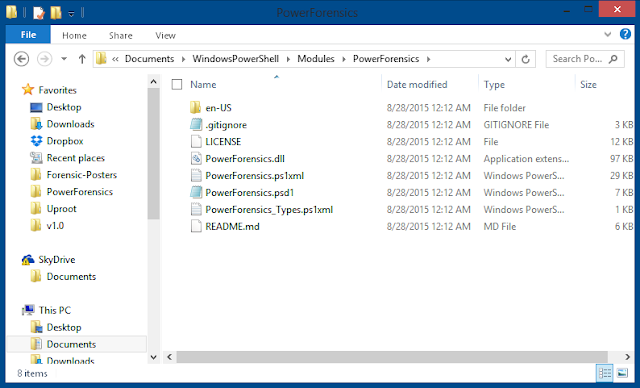
Invoke-Item (Get-UserModulePath)Extract the archive to the PowerForensics folder. When you are done you should have all these files in your PowerForensics directory:
Start a new PowerShell session and import the PowerForensics module using the commands below:
Get-Module -ListAvailable -Name PowerForensics
Import-Module PowerForensics
Get-Command -Module PowerForensicsYou are now ready to use the PowerForensics PowerShell module!
Getting Started
- PowerForensics
- PowerForensics.Artifacts
- PowerForensics.Ntfs
- PowerForensics.Formats
- PowerForensics.Registry
- PowerForensics.Utilities
Cmdlets
- ConvertTo-ForensicTimeline
- Copy-ForensicFile
- Get-ForensicAlternateDataStream
- Get-ForensicAmcache
- Get-ForensicAttrDef
- Get-ForensicBitmap
- Get-ForensicBootSector
- Get-ForensicChildItem
- Get-ForensicContent
- Get-ForensicEventLog
- Get-ForensicFileRecord
- Get-ForensicFileRecordIndex
- Get-ForensicFileSlack
- Get-ForensicGuidPartitionTable
- Get-ForensicMasterBootRecord
- Get-ForensicMftSlack
- Get-ForensicNetworkList
- Get-ForensicPartitionTable
- Get-ForensicPrefetch
- Get-ForensicRegistryKey
- Get-ForensicRegistryValue
- Get-ForensicScheduledJob
- Get-ForensicSid
- Get-ForensicTimeline
- Get-ForensicTimezone
- Get-ForensicUnallocatedSpace
- Get-ForensicUserAssist
- Get-ForensicUsnJrnl
- Get-ForensicUsnJrnlInformation
- Get-ForensicVolumeBootRecord
- Get-ForensicVolumeInformation
- Get-ForensicVolumeName
- Invoke-ForensicDD