-
Notifications
You must be signed in to change notification settings - Fork 234
Home
Welcome to Medusa's wiki. Please use the sidebar to navigate to a section:
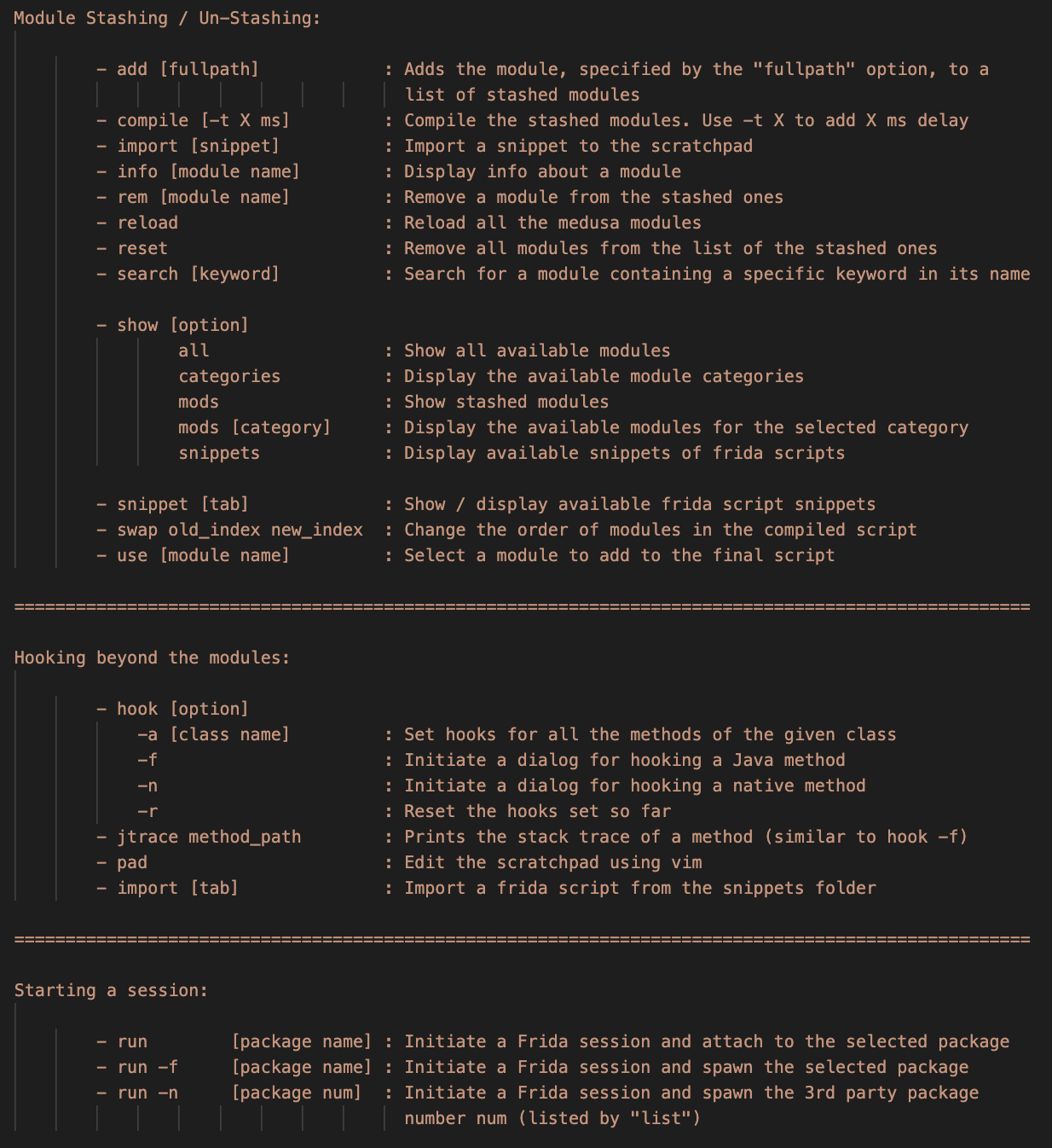
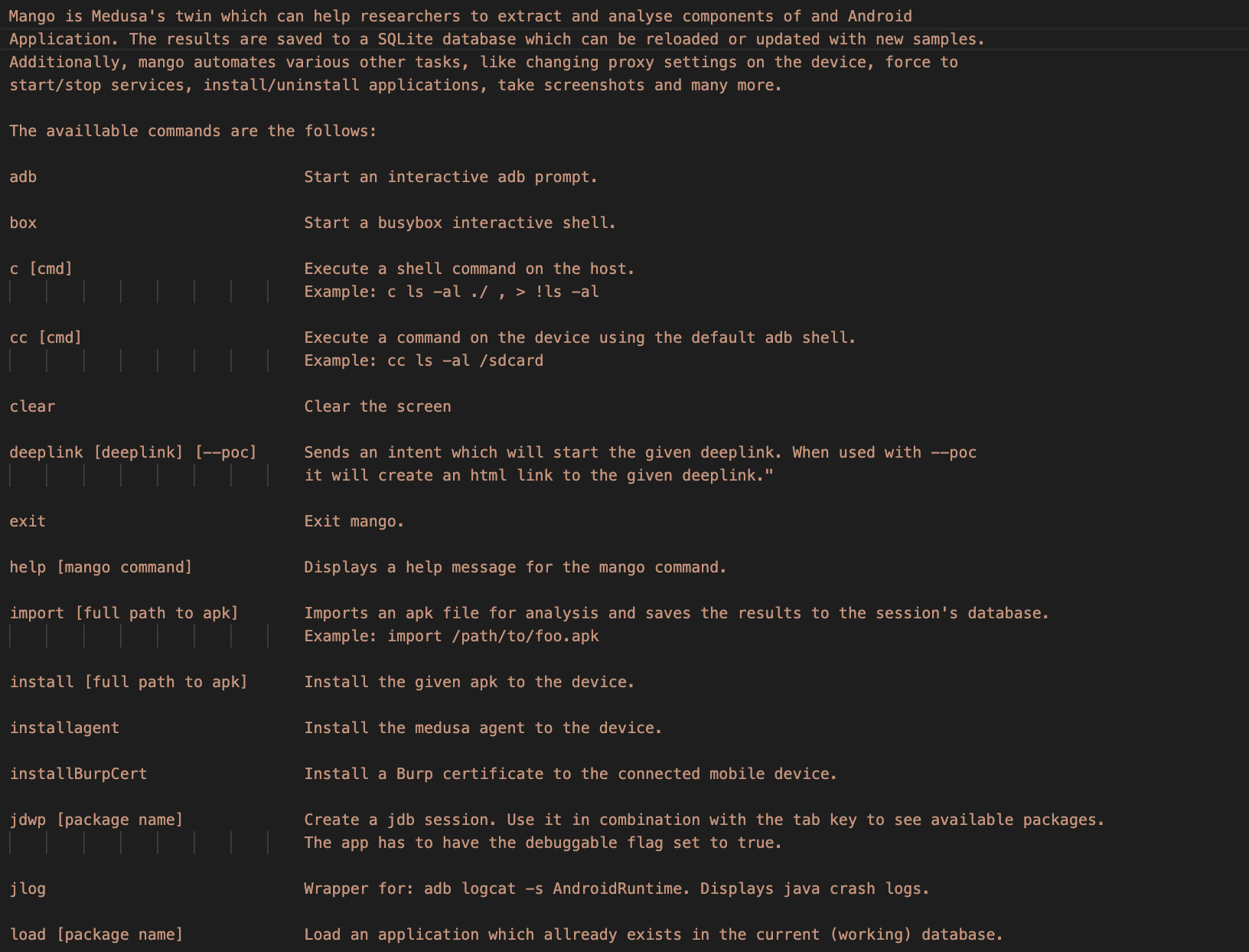
Use the show command, followed one of the following options:
- all to Display all available modules
- mods to Display stashed modules
- categories to Display the available module categories
- mods [category] to Display the available modules for the selected category
Use the info [module name]to get help about a specific module
- Use the
use [module name]to add a module to the stashed ones:
medusa> use http_communications/multiple_unpinner
- Use the
rem [module name]to remove a module to the stashed ones
medusa> rem http_communications/multiple_unpinner
- Use the
add [full-path-to-module]to stash modules saved out of the default directory
medusa> add /full/path/to/module.med
-
Use the
resetto empty the list of stashed modules and clear the unified script -
Use the
swapto change the compilation order of the stashed modules:
medusa> swap [index 1] [index 2]
- Use the
compileto compile your stashed modules to a unified one:
medusa> compile
- Use the
compile -t X(X is the delay value in milliseconds) to add a loading delay:
medusa> compile -t 1000
- Use the
run -f [package name]or torun -n [package number]to start or restart an application and attach to it (you can use thelistcommand to get the package number).
medusa> run -f com.foo.bar
- Use the
run [package name]to attach to an application.
[in-session] |c:clear |e:exit |r:reload | | rs:reset scratchpad |i:info |t:trace |?:help |:
While 'in session' you can use one of the following commands:
'c' (c)lear the sreen
'e' (e)xit the session
'r' (r)eload the script in case it changed
'rs' (r)e(s)et the scratchpad
'i' print (i)nformation about the application
't' (t)race a function and print the stack trace (e.g. t com.foo.bar.func)
'?' print this help message
- Use the
hookcommand followed by one of the options bellow to intercept methods which are not present in the currently available modules:
-a [class name] : Set hooks for all the methods of the given class. Example:
medusa> hook -a com.foo.bar.className
-f : Set hooks for a single method. Example
medusa> hook -f
Enter the full name of the method(s) class: com.foo.bar
Enter a method name (CTRL+C to Exit): fooMethod
Enable backtrace? (y/N) y
[+] Method: fooMethod hook added !
Enter a method name (CTRL+C to Exit):
Same result can be achieved with the jtrace command: medusa> jtrace full_path_to_method
-n : Set hooks for a native method. Example
medusa> hook -n
Library name (e.g.: libnative.so): libfoo.so
Imported or exported function? (i/e) e
Function name or offset (e.g.: 0x1234): 0x1234
Number of function arguments (0 to disable trace): 3
Enable backtrace? (y/N) y
Enable memory read? (y/N) y
Read Buffer size (0-1024): 128
Module scratchpad already added !
-r: Reset the hooks set so far
- Use the
padcommand to edit the scratchpad
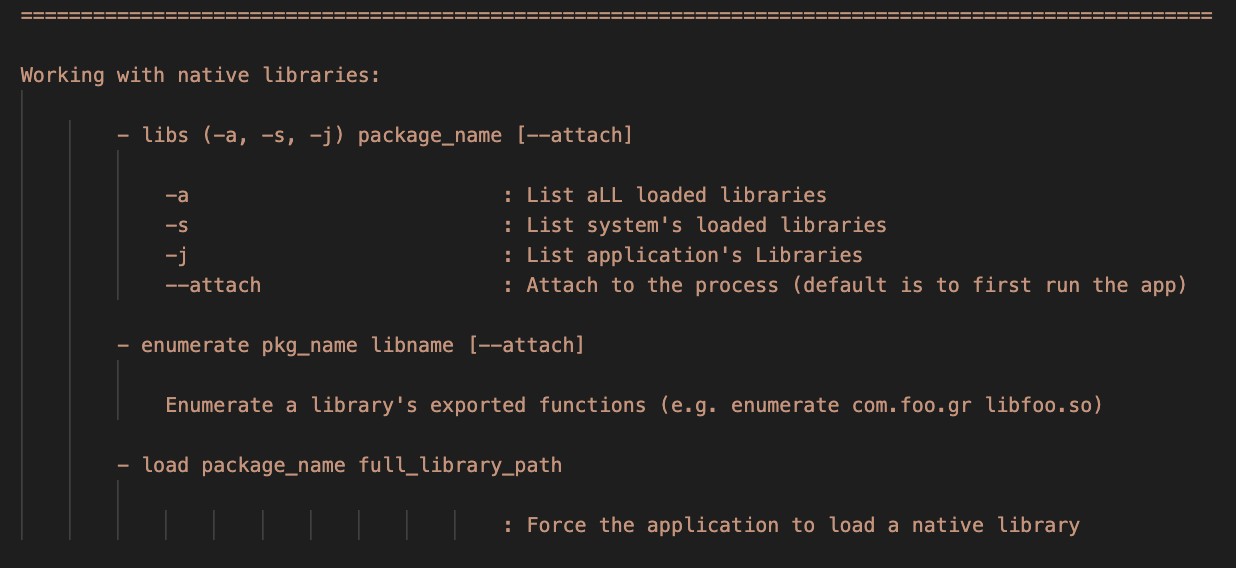
- Use the
libscommand followed by one of the options bellow to list the application's native libraries:
-a : List all the application's libraries.
-s : List only the system's libraries.
-j : List only the application's libraries.
Add the --attach to attach to an already running instance of the application (usually has better results)
Example:
medusa> libs -j com.foo.bar libnative.so --attach
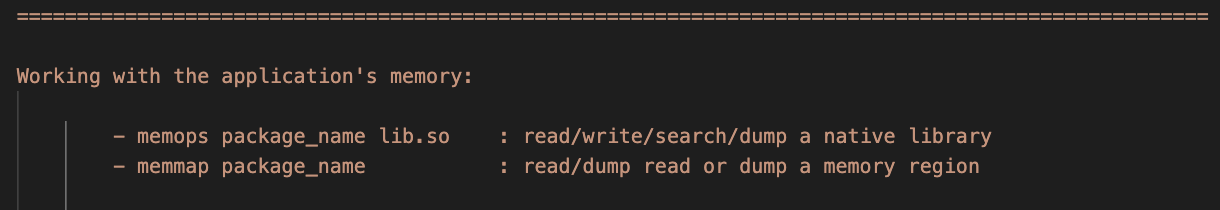
You can read/write/search/dump the application's memory by using the memops or memmap command. The former needs a library name to be attached to, while the later uses memory regions.
In both cases the application must already be running !
- memops example:
medusa> memops package_name libname.so
If the attachment is successful, medusa will start a session where you have the following options:
|(E)xit |r@offset |w@offset |⏎ |scan |(h)elp| dump|:
To get more details about the functionality of each option, please refer to the Basic Usage section
- memmap example:
medusa> memmap package_name
Then choose a memory region from the submenu.
If the attachment is successful, medusa will start a session where you have the following options:
|(E)xit |r@offset |dump |:
To get more details about the functionality of each option, please refer to the Basic Usage section
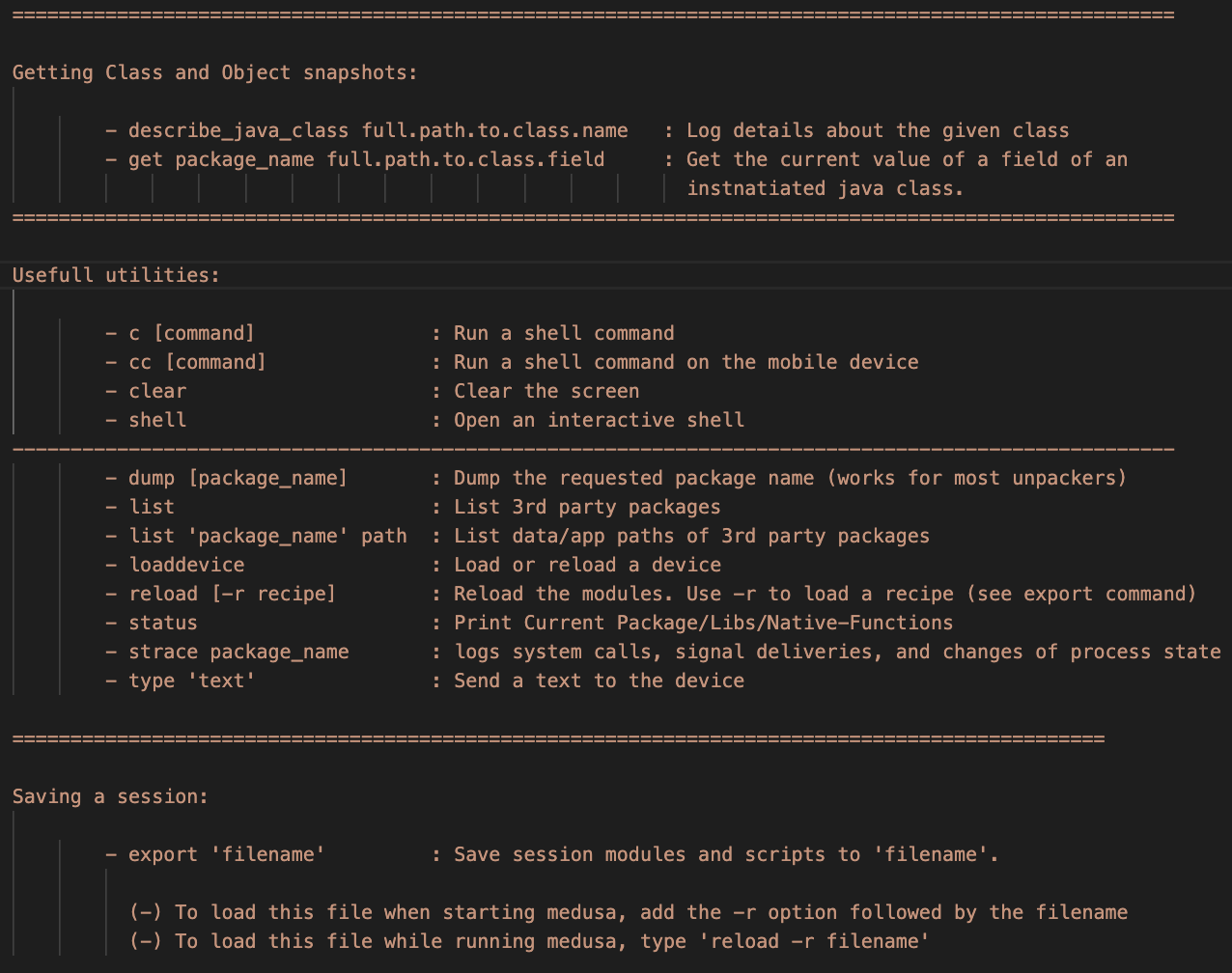
Use the describe_java_class to print a class's details, example:
medusa> describe_java_class full.path.to.class.name
Use the get to print the value of a field of a class, assuming that the class has been instantiated.
medusa> get package_name full.path.to.class.field
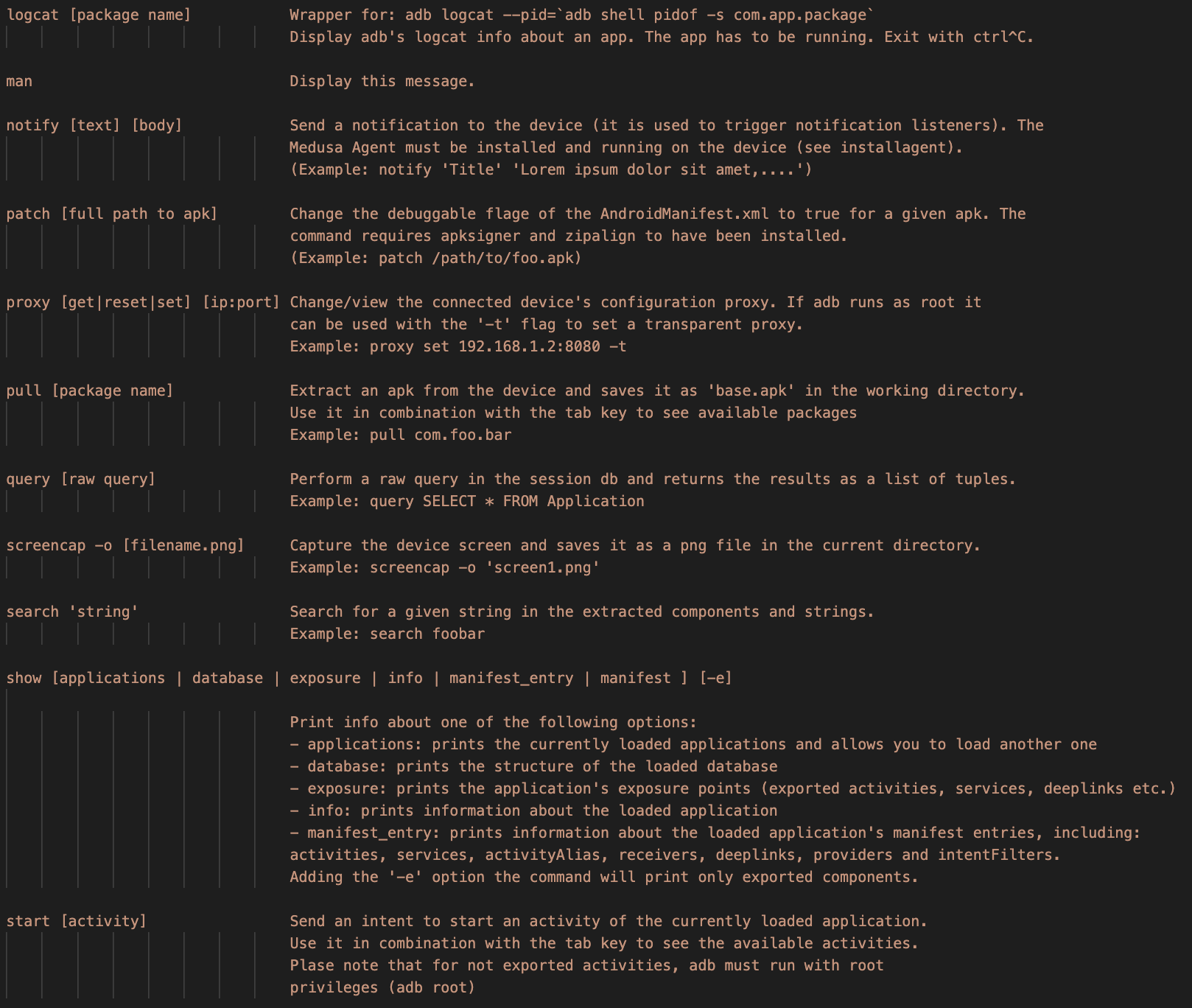
- Run a shell command
medusa> c ls -al
- Run a shell command to the connected device
medusa> cc ls -al
- Clear the screen
medusa> clear
- Open an interactive shell
medusa> clear
- Dump the dex files of an app
medusa> dump com.foo.bar
- List the installed packages
medusa> list
- List the paths of a package
medusa> list com.foo.bar path
- Load or reload a device:
medusa> loaddevice
- Reload the medusa modules. This option is useful in case you made a change to a medusa module.
medusa> reload
- Load a saved session
medusa> reload -r session-filename
- Print the current session status
medusa> status
- Log system calls
medusa> strace package_name
- Send text to the device
medusa> type 'text'
- Save the current session
medusa> export file-name
To load back this session use one of the following options:
-
./medusa -r file-name -
medusa> reload -r file-name
- You can use an existing session file as an argument to the mango script (./mango session_file) or start mango without arguments and follow the prompt:
--------------------------------------------------
[?] What do you want to do ?
--------------------------------------------------
1 Start a new session
2 Continue an existing session
3 Exit
- You can import:
- A downloaded APK:
mango> import /full/path/to/foo.apk - An APK installed in the connected device:
mango> pull package_nameand thenmango>import base.apk
- A downloaded APK:
- Or reload an APK that has already been analysed
mango> load package_name
- You can view an application's components (activities, services etc.) by using the
showcommand followed by the component type.
Example:
mango> show activities
Other options are: activityAlias, services, receivers, providers, permissions, deeplinks and intentFilters.
Using the -e (when applicable) will print only the exported components.
-
Further than that, the
showcommand supports the following additional options:- exposure : Prints the application's "attack surface", including deeplinks, exported activities, activity aliases, services, receivers and providers.
- info : Prints handy information about the loaded application
- strings : Prints the application's string resources
- database : Prints the structure of the database file. The output can be used to construct raw sql queries (see query command).
- applications : This option can be used to load a different application or manage the existing applications.
-
You can issue "raw" SQL queries to the db of your current session by typing
queryfollowed by the query body:
query select permission, type from Permissions where app_sha256="a2e5bfac992ecac9c3b7013294936517330e9f6b2cfb1b6b98bf9a366eb31ff0"
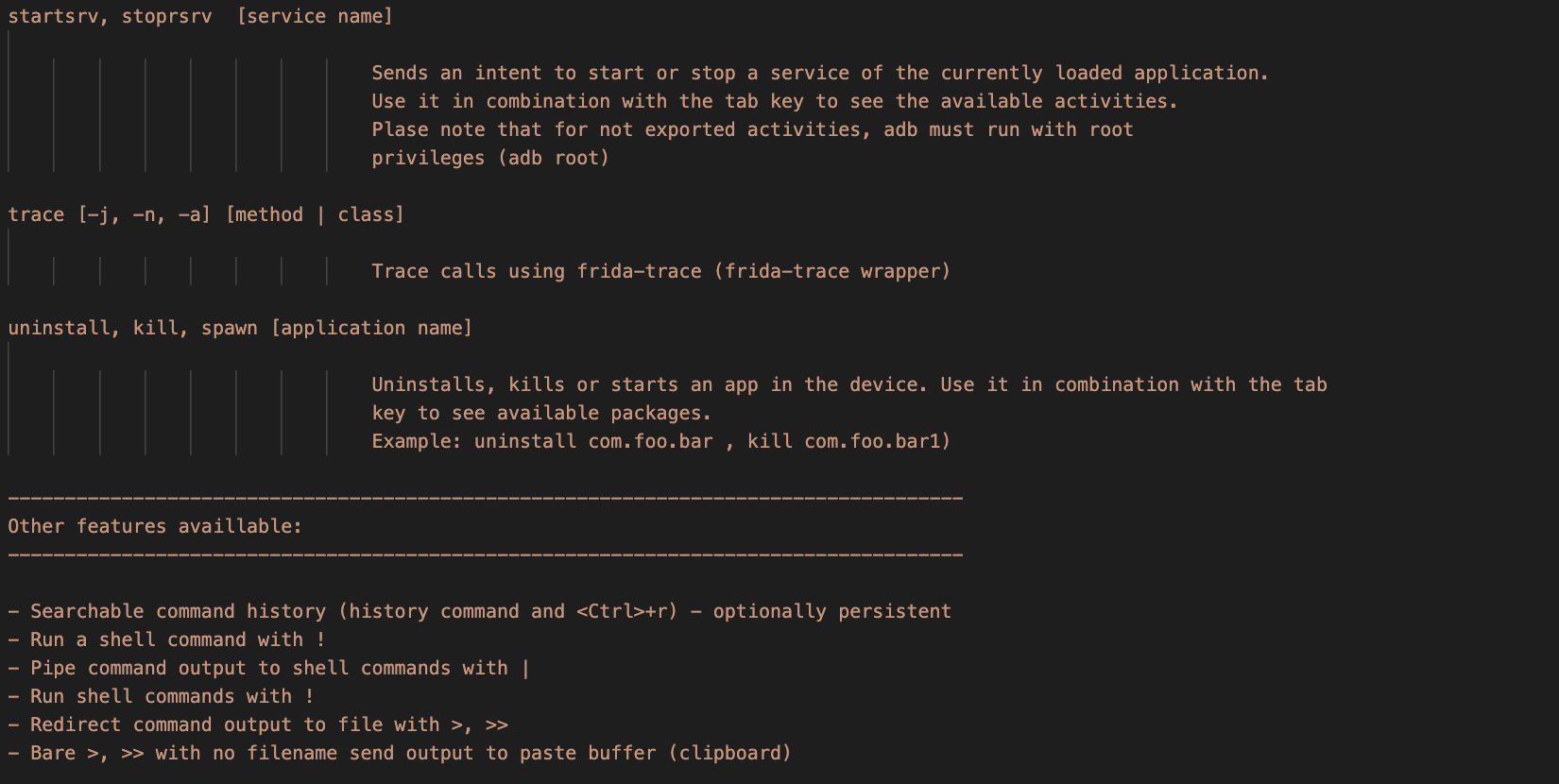
- You can force the currently loaded application to start an activity by typing start followed by tab or the full name of an activity:
mango> start com.foo.bar.ActivityA
- Similarly you can force the application to start a service by typing startsrv followed by tab or the full name of a service:
mango> startsrv com.foo.bar.serviceA
Or stop a service by typing:
mango> stopsrv com.foo.bar.serviceA
- To trigger a deeplink, type deeplink followed by tab or the full uri of the deeplink:
mango> deeplink example://mywebview
- Additionally, you can kill or start an application by typing kill or spawn respectively followed by the application's name:
mango> spawn com.example.package
- To install an application use the
mango> install /full/path/to/foo.ak - To uninstall an application use the
mango> uninstall [package name] - To install a burp certificate, type
installBurpCertand follow the steps indicated by mango - To modify the device's proxy settings, type
proxyfollowed by one of the following options: - get to print the current proxy configuration
- set ip:port to set a proxy configuration. Adding -t (e.g. mango> proxy set -t 192.168.1.2:8080 will set a transparent proxy
- reset will clear the device's proxy
- To start an interactive adb session, type
adb - To start an interactive shell with busybox support type
boxand follow the given instructions - To get a package specific logcat, type
logcat [package name]. You can also get the device's native logs by usingnlogor the Java crash logs by usingjlog - To get a screenshot, type
screencap -o [filename.png] - To run a shell command to the connected device, type:
cc [command] - You can send a notification to the device by typing notify notification_title notification_body. The command requires the installation of the medusa agent which can be done by using the
ìnstallagentcommand.
- Set the debuggable flag to true of a given APK:
patch /full/path/to/foo.apk
This option requires the apksigner and zipalign to be installed in the device. If they aren't mango will download them locally and use them.
-
Dynamically debug an app using the
jdwp [package name] -
Start a frida-trace session, using the
tracecommand and one of the following options: -
-jto trace all the functions of a java class. Example:trace -j com.myapp.name* // Trace all the functions of the com.myapp.name* class -
-nto trace a native function. Example:trace -n name* -
-ato trace the all the functions of a native library. Exampletrace -a libfoo.so
You can contribute to this project by:
- Making a pull request to add a cool feature or make an improvement
- Creating a medusa module (see how to)
- Reporting an error/issue
- Suggesting an improvement
- Making this project more popular by sharing it or giving a star
- Buying a treat:
Bitcoin (BTC) Address: bc1qhun6a7chkav6mn8fqz3924mr8m3v0wq4r7jchz
Ethereum (ETH) Address: 0x0951D1DD2C9F57a9401BfE7D972D0D5A65e71dA4
Medusa Wiki
Medusa Wiki
-
- Searching for the right module
- Getting info about a module
- Stashing / un-stashing
- Compiling
- Starting a session
- Hooking beyond the modules
- Importing Frida scripts
- Working with native libraries
- Working with the application's memory
- Getting Class and Object snapshots
- Useful utilities
- Saving a session (recipe)