-
Notifications
You must be signed in to change notification settings - Fork 578
[Examples] Deploy Default Configuration
This example code will deploy the minimum recommended management group and subscription organization from the Azure landing zone conceptual architecture. You can then start to customize your deployment once you've got this up and running.
This is a good starting point when first discovering what resources are created by this module.
IMPORTANT: Ensure the module version is set to the latest, and don't forget to run
terraform initif upgrading to a later version of the module.
TIP: Although only
root_parent_idis required, we recommend settingroot_idandroot_nameto something more meaningful. Changingroot_idwill result in the entire deployment to be re-provisioned.
To keep things simple, the root module for this example is based on a single file:
# We strongly recommend using the required_providers block to set the
# Azure Provider source and version being used.
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "~> 3.107"
}
}
}
provider "azurerm" {
features {}
}
# You can use the azurerm_client_config data resource to dynamically
# extract connection settings from the provider configuration.
data "azurerm_client_config" "core" {}
# Call the caf-enterprise-scale module directly from the Terraform Registry
# pinning to the latest version
module "enterprise_scale" {
source = "Azure/caf-enterprise-scale/azurerm"
version = "<version>" # change this to your desired version, https://www.terraform.io/language/expressions/version-constraints
default_location = "<YOUR_LOCATION>"
providers = {
azurerm = azurerm
azurerm.connectivity = azurerm
azurerm.management = azurerm
}
root_parent_id = data.azurerm_client_config.core.tenant_id
root_id = "myorg"
root_name = "My Organization"
}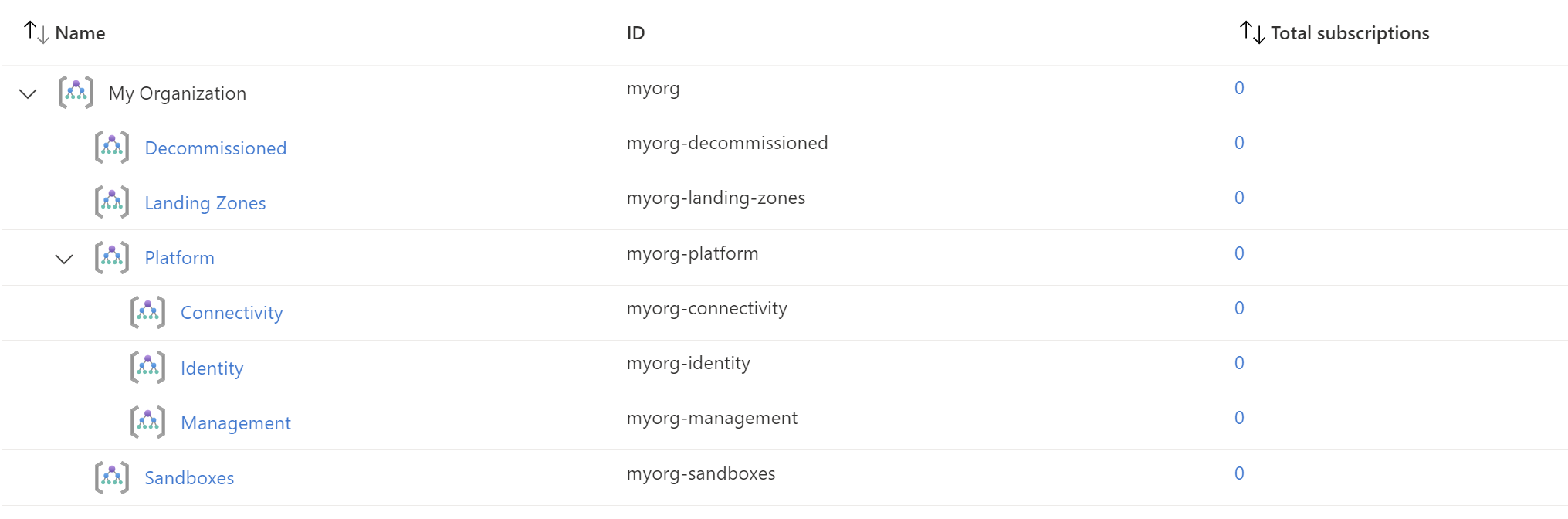
You have successfully created the default Management Group resource hierarchy, along with the recommended Azure Policy and Access control (IAM) settings for your Azure landing zone.
TIP: The exact number of resources created depends on the module configuration, but you can expect upwards of 200 resources to be created by this module for a default installation.
Go to our next example to learn how to deploy the demo landing zone archetypes.
This wiki is being actively developed
If you discover any documentation bugs or would like to request new content, please raise them as an issue or feel free to contribute to the wiki via a pull request. The wiki docs are located in the repository in the docs/wiki/ folder.
- Home
- User guide
- Video guides
-
Examples
- Level 100
- Level 200
-
Level 300
- Deploy multi region networking with custom settings (Hub and Spoke)
- Deploy multi region networking with custom settings (Virtual WAN)
- Deploy with Zero Trust network principles (Hub and Spoke)
- Deploy identity resources with custom settings
- Deploy management resources with custom settings
- Expand built-in archetype definitions
- Create custom policies, initiatives and assignments
- Override module role assignments
- Control policy enforcement mode
- Policy assignments with user assigned managed identities
- Level 400
- Frequently Asked Questions
- Troubleshooting
- Contributing
