diff --git a/examples/centralized_design/README.md b/examples/centralized_design/README.md
index 0c00260..8393886 100644
--- a/examples/centralized_design/README.md
+++ b/examples/centralized_design/README.md
@@ -10,7 +10,7 @@ The Terraform code presented here will deploy Palo Alto Networks VM-Series firew
## Reference Architecture Design
-
+
This code implements:
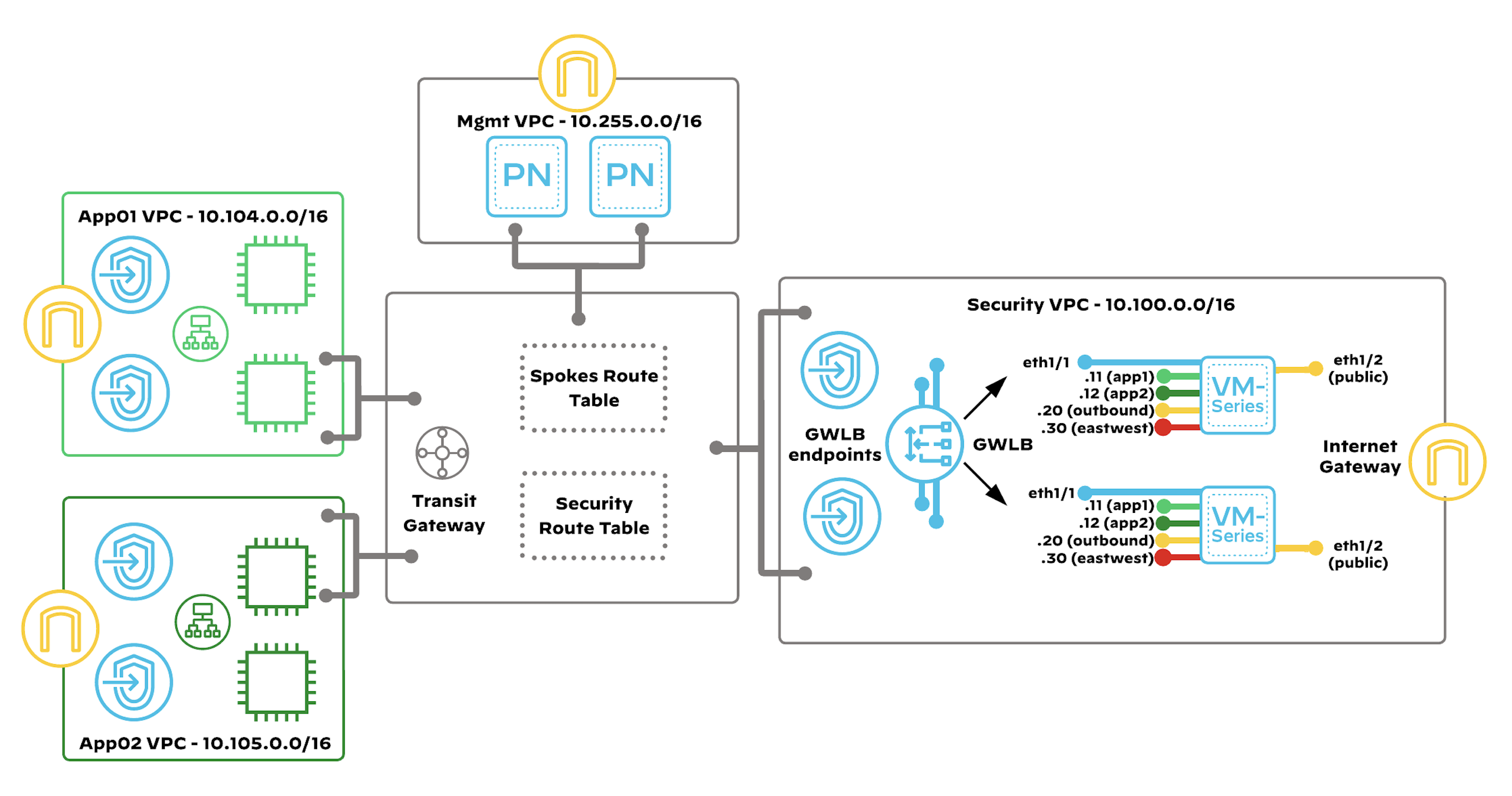
- a _centralized design_, which secures outbound, inbound, and east-west traffic flows using an AWS transit gateway (dTGW). Application resources are segmented across multiple VPCs that connect in a hub-and-spoke topology, with a dedicated VPC for security services where the VM-Series are deployed
@@ -21,7 +21,7 @@ This code implements:
This design supports interconnecting a large number of VPCs, with a scalable solution to secure outbound, inbound, and east-west traffic flows using a transit gateway to connect the VPCs. The centralized design model offers the benefits of a highly scalable design for multiple VPCs connecting to a central hub for inbound, outbound, and VPC-to-VPC traffic control and visibility. In the Centralized design model, you segment application resources across multiple VPCs that connect in a hub-and-spoke topology. The hub of the topology, or transit gateway, is the central point of connectivity between VPCs and Prisma Access or enterprise network resources attached through a VPN or AWS Direct Connect. This model has a dedicated VPC for security services where you deploy VM-Series firewalls for traffic inspection and control. The security VPC does not contain any application resources. The security VPC centralizes resources that multiple workloads can share. The TGW ensures that all spoke-to-spoke and spoke-to-enterprise traffic transits the VM-Series.
-
+
## Prerequisites
diff --git a/examples/centralized_design_autoscale/README.md b/examples/centralized_design_autoscale/README.md
index 023927e..d508b01 100644
--- a/examples/centralized_design_autoscale/README.md
+++ b/examples/centralized_design_autoscale/README.md
@@ -10,7 +10,8 @@ The Terraform code presented here will deploy Palo Alto Networks VM-Series firew
## Reference Architecture Design
-
+
+
This code implements:
- a _centralized design_, which secures outbound, inbound, and east-west traffic flows using an AWS transit gateway (TGW). Application resources are segmented across multiple VPCs that connect in a hub-and-spoke topology, with a dedicated VPC for security services where the VM-Series are deployed
@@ -20,7 +21,7 @@ This code implements:
### Centralized Design
This design supports interconnecting a large number of VPCs, with a scalable solution to secure outbound, inbound, and east-west traffic flows using a transit gateway to connect the VPCs. The centralized design model offers the benefits of a highly scalable design for multiple VPCs connecting to a central hub for inbound, outbound, and VPC-to-VPC traffic control and visibility. In the Centralized design model, you segment application resources across multiple VPCs that connect in a hub-and-spoke topology. The hub of the topology, or transit gateway, is the central point of connectivity between VPCs and Prisma Access or enterprise network resources attached through a VPN or AWS Direct Connect. This model has a dedicated VPC for security services where you deploy VM-Series firewalls for traffic inspection and control. The security VPC does not contain any application resources. The security VPC centralizes resources that multiple workloads can share. The TGW ensures that all spoke-to-spoke and spoke-to-enterprise traffic transits the VM-Series.
-
+
### Auto Scaling VM-Series
diff --git a/examples/combined_design/README.md b/examples/combined_design/README.md
index 8d279da..d60753b 100644
--- a/examples/combined_design/README.md
+++ b/examples/combined_design/README.md
@@ -10,7 +10,8 @@ The Terraform code presented here will deploy Palo Alto Networks VM-Series firew
## Reference Architecture Design
-
+
+
This code implements:
- a _centralized design_, which secures outbound, inbound, and east-west traffic flows using an AWS transit gateway (TGW). Application resources are segmented across multiple VPCs that connect in a hub-and-spoke topology, with a dedicated VPC for security services where the VM-Series are deployed
@@ -25,7 +26,7 @@ This design supports interconnecting a large number of VPCs, with a scalable sol
Inbound traffic originates outside your VPCs and is destined to applications or services hosted within your VPCs, such as web or application servers. The combined model implements inbound security by using the VM-Series and Gateway Load Balancer (GWLB) in a Security VPC, with distributed GWLB endpoints in the application VPCs. Unlike with outbound traffic, this design option does not use the transit gateway for traffic forwarding between the security VPC and the application VPCs.
-
+
## Prerequisites
diff --git a/examples/combined_design_autoscale/README.md b/examples/combined_design_autoscale/README.md
index 0665015..1ab0a33 100644
--- a/examples/combined_design_autoscale/README.md
+++ b/examples/combined_design_autoscale/README.md
@@ -10,7 +10,8 @@ The Terraform code presented here will deploy Palo Alto Networks VM-Series firew
## Reference Architecture Design
-
+
+
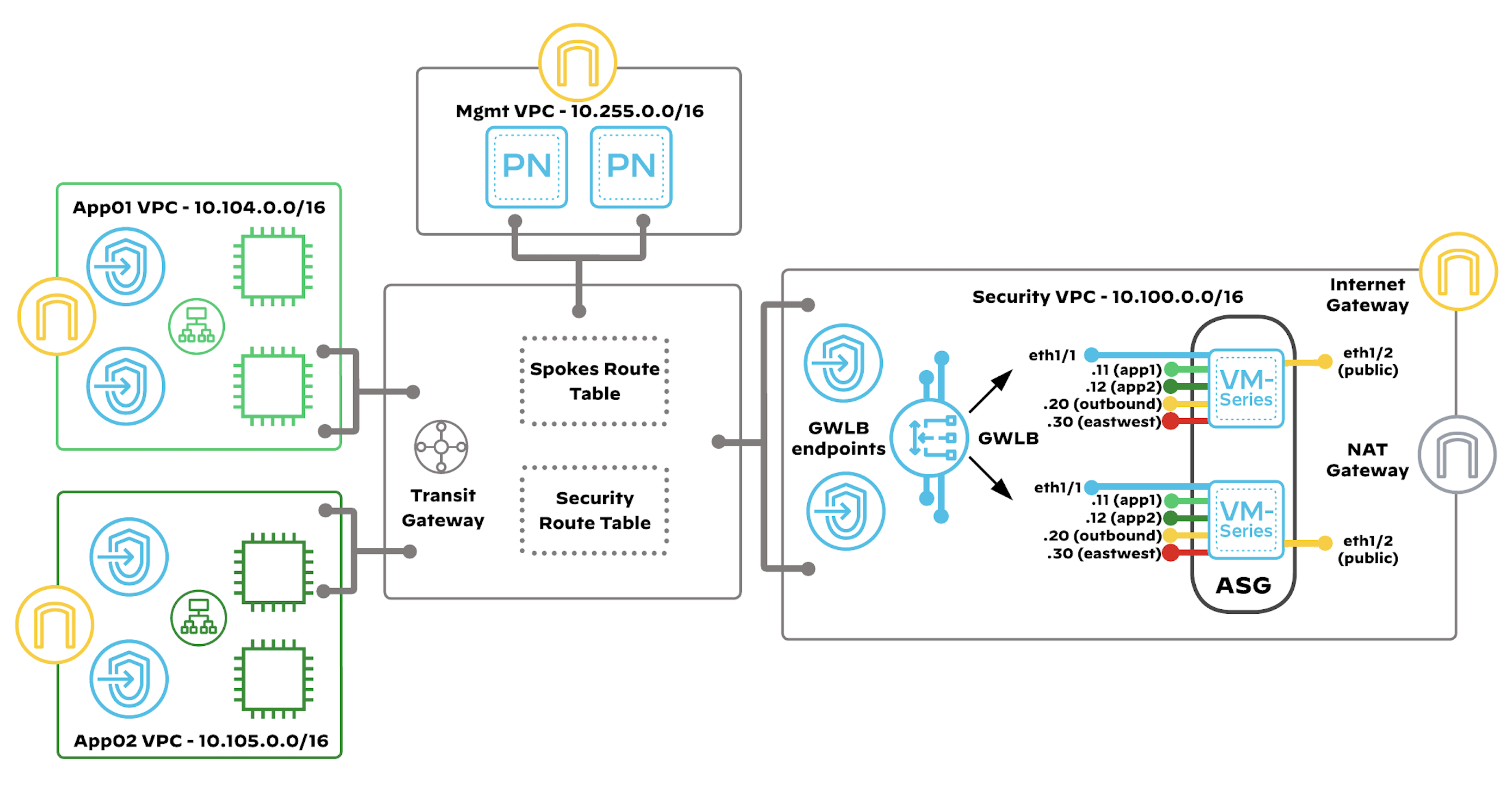
This code implements:
- a _centralized design_, which secures outbound, inbound, and east-west traffic flows using an AWS transit gateway (TGW). Application resources are segmented across multiple VPCs that connect in a hub-and-spoke topology, with a dedicated VPC for security services where the VM-Series are deployed
@@ -26,7 +27,7 @@ This design supports interconnecting a large number of VPCs, with a scalable sol
Inbound traffic originates outside your VPCs and is destined to applications or services hosted within your VPCs, such as web or application servers. The combined model implements inbound security by using the VM-Series and Gateway Load Balancer (GWLB) in a Security VPC, with distributed GWLB endpoints in the application VPCs. Unlike with outbound traffic, this design option does not use the transit gateway for traffic forwarding between the security VPC and the application VPCs.
-
+
### Auto Scaling VM-Series
diff --git a/examples/isolated_design/README.md b/examples/isolated_design/README.md
index 44a37f2..f559e63 100644
--- a/examples/isolated_design/README.md
+++ b/examples/isolated_design/README.md
@@ -11,7 +11,8 @@ The Terraform code presented here will deploy Palo Alto Networks VM-Series firew
## Reference Architecture Design
-
+
+
This code implements:
- an _isolated design_, which secures outbound and inbound traffic flows using AWS Gateway Load Balancer (GWLB). Application resources are segmented across multiple VPCs that distribute traffic to the dedicated VPC for security services where the VM-Series are deployed.
@@ -26,8 +27,8 @@ The Isolated Design model centralizes the security instances in a dedicated secu
Inbound traffic originates outside the VPC and is destined to applications or services hosted within your VPCs, such as web servers. This design uses the GWLB and VM-Series firewalls in the security VPC, with GWLB endpoints in the application VPCs for the transparent inspection of inbound traffic.
+
-
## Prerequisites
diff --git a/examples/isolated_design_autoscale/README.md b/examples/isolated_design_autoscale/README.md
index 64f661f..0357f48 100644
--- a/examples/isolated_design_autoscale/README.md
+++ b/examples/isolated_design_autoscale/README.md
@@ -10,7 +10,7 @@ The Terraform code presented here will deploy Palo Alto Networks VM-Series firew
## Reference Architecture Design
-
+
This code implements:
- an _isolated design_, which secures outbound and inbound traffic flows using AWS Gateway Load Balancer (GWLB). Application resources are segmented across multiple VPCs that distribute traffic to the dedicated VPC for security services where the VM-Series are deployed.
@@ -22,7 +22,7 @@ The Isolated Design model centralizes the security instances in a dedicated secu
Inbound traffic originates outside the VPC and is destined to applications or services hosted within your VPCs, such as web servers. This design uses the GWLB and VM-Series firewalls in the security VPC, with GWLB endpoints in the application VPCs for the transparent inspection of inbound traffic.
-
+
### Auto Scaling VM-Series
diff --git a/examples/panorama_standalone/README.md b/examples/panorama_standalone/README.md
index 0dd2781..0a65e10 100644
--- a/examples/panorama_standalone/README.md
+++ b/examples/panorama_standalone/README.md
@@ -16,7 +16,7 @@ The topology consists of :
- VPC with 2 subnets in 2 availability zones
- 2 Panorama instances with a public IP addresses and static private IP addresses
-
+
## PAN-OS software version
diff --git a/examples/vmseries_standalone/README.md b/examples/vmseries_standalone/README.md
index 769ec8d..00cf0a1 100644
--- a/examples/vmseries_standalone/README.md
+++ b/examples/vmseries_standalone/README.md
@@ -21,7 +21,7 @@ The topology consists of :
- VPC with 1 subnet in 1 availability zones
- 1 VM-Series instances with a public IP address and static private IP address
- +
+ ## PAN-OS software version
## PAN-OS software version